HTB - Pro Labs - Dante
Intro #

Dante is a Pro Lab, available on Hack the Box, that has been designed and labelled to be beginner friendly. Now in true HTB fashion, easy/beginner does not mean what readers may think it means. In the perspective of HTB difficulty, yes it probably does match that, but if I came into this blind - I would not have rated it that. Let’s review…
Review #
As I’ve mentioned in a different post, I don’t do anything technical or offensive in my normal day job anymore. Yes, I’m surrounded by CyberSecurity and application security, but I don’t actually get to do anything. So a nice compromise recently has been to spend time hacking on things in my downtime. I bought access to the Pro Labs and decided to run through Dante as a ‘welcome back’ challenge.
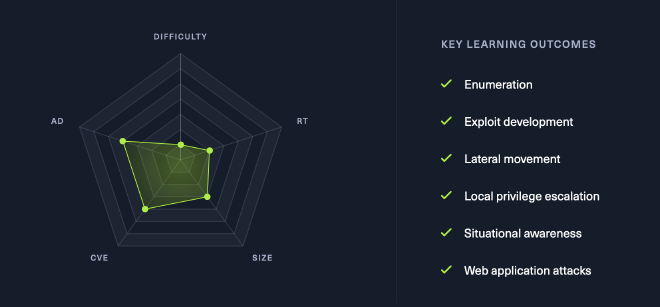
The lab has 13 machines, across 2 different internal networks, a total of 26 flags available. There is a selection of systems that run web servers, and some that only run ‘management’ services, such as SSH (etc). A wide range of users to target, passwords to be found, dumped and cracked and the lab even includes so custom exploit requirements (specifically buffer overflows).
As an immediate warning/heads up, the pro labs are a shared environment. So although you are hacking from your own machine, when you land on a box and start enumerating them, it is likely you will find other peoples tools, scripts, information. You may find spoilers, artefacts left over from other users, missing flags (yes, some people delete them because they’re edgey). It’s a little frustrating considering you are paying extra to use the systems, but stick with it, and worse case, change your VPN server and try a different one.
Now back to the boxes… as an app guy, the web server boxes were fairly trivial. Some of the obstacles were a little hidden, but they were pretty quick to fall once enumeration steps were followed. With each foothold, comes a form of privilege escalation and then post exploitation steps. This is where I never really get a chance to learn and develop, so it was more of a challenge for me personally… however, the obstacles weren’t so bad once the correct path was found.
Beyond the web application issues, Dante offers a selection of escalation techniques that require knowledge of both Linux and Windows, as well as their internal services. The networks ran a selection of Linux and Windows boxes, with some domain joined machines and some standalone to help the attacker get a feel for hacking both.
The ’easy’ tag likely refers to the fact that most of the techniques and attacks used are fairly common, and the ones mostly talked about. For example, if you hear someone talking about a Domain Controller in Windows Active Directory, the mind quickly runs to something like Kerberoasting.
When it comes to ‘CTF’, I wouldn’t say this lab was full of them. There was one specific challenge I felt was a little too guess-y/bruteforce-y for a lab that was supposed to resemble a company network, but once I had overcome that challenge I thought about it and honestly, I’ve come across it in a real world test. It just felt dumb at the time (but I guess most human weaknesses/issues are!) With this in mind, I would recommend having a copy of Rocktastic on your system and just remember that CeWL exists!
A key take away for me when working on Dante was the required network pivoting. Although I have done it in the past, for example during my OSCP exam, I had never really understood it. I usually just targetted getting a shell, reverse SSH-ing back to my box and hoping proxychains did the rest. But in Dante, it really made me step back and figure out how to set up a chain that would allow me to hit all boxes. A collection of chains were used throughout the lab, some boxes required multiple hops from my attacker system - so knowing how it worked really helped open up opportunities for my traffic. This for me was the biggest take away, and true value of this entire lab. A massive win was learning and using Chisel. Not only is it written in Go, but it works flawlessly across multiple operating systems, is fast, and I didn’t hit any issues/errors at all during usage. Between Chisel and ProxyChains, I was pivoting and tunneling my way through the environment. I would highly recommend it!
Final Thoughts #
Overall, I would recommend Dante, but don’t approach it thinking it is going to be one big AD environment. I initially thought this, and I was surprised to find a bunch of things that had nothing to do with it. What I will say, is this lab covers pretty much everything I had to do during my OSCP (lab and exam). So if you are preparing for that challenge, then Dante will likely be a great resource for you. If you can finish up in 1 month, it’ll cost you under £50, which honestly, for a playground of this size and depth, is very much worth it!